This version of the OpenSearch documentation is no longer maintained. For the latest version, see the current documentation. For information about OpenSearch version maintenance, see Release Schedule and Maintenance Policy.
Setting up Security Analytics
Before Security Analytics can begin generating findings and sending alerts, administrators must create detectors and make log data available to the system. Once detectors are able to generate findings, you can fine-tune your alerts to focus on specific areas of interest. The following steps outline the basic workflow for setting up components in Security Analytics.
- Create security detectors and alerts, and ingest log data. See Creating detectors for details.
- Inspect findings generated from detector output and create any additional alerts.
- If desired, create custom rules by duplicating and then modifying pre-packaged rules. See Customizing rules for details.
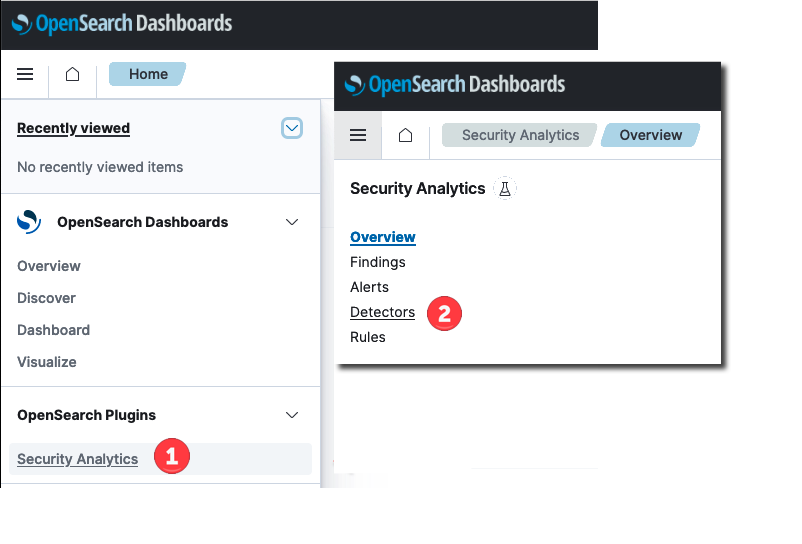
Navigate to Security Analytics
- To get started, select the top menu on the Dashboards home page and then select Security Analytics. The Overview page for Security Analytics is displayed.
- From the options on the left side of the page, select Detectors to begin creating a detector.